What is a System Security Plan?

The SSP has been part of the NIST 800-171 security requirement set forth by DFARS 7012, and the DoD’s newer Cybersecurity Maturity Model Certification (CMMC) also mandates it. Six Steps to Attaining CMMC Compliance for DoD Contractors.
An SSP is a document that outlines the policies, procedures, and controls that are in place to protect an organization's systems and data from unauthorized access and attacks.
SSPs typically include:
- Cybersecurity policies and procedures
- Controls to protect against threats
- Roles and responsibilities of the individuals and teams involved in managing the organization's cybersecurity.
To comply with NIST 800-171 or CMMC, an organization must have an SSP in place and adhere to the security controls and procedures outlined within it. In addition, the SSP should be regularly reviewed and updated to ensure that it continues to meet the evolving security needs of the organization and regulatory requirements.
Why are SSPs important for NIST 800-171 and CMMC compliance?
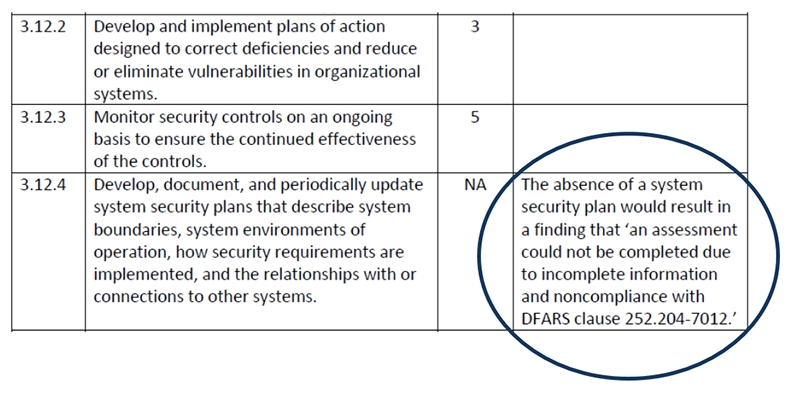
NIST 800-171 and CMMC require organizations to have an SSP for cybersecurity compliance. The SSP is used to assess the organization's security posture and identify any gaps or weaknesses that it must address to meet these standards' requirements. An SSP is a requirement of NIST 800-171 and a must-have for a company to submit a NIST 800-171 assessment score. NIST 800-171 control 3.12.4 states:
Benefits of SSPs
In addition to meeting the requirements of NIST 800-171 and CMMC, SSPs also provide other benefits for organizations.
SSPs help to ensure the organization's security measures are always up-to-date and effective. The SSP also provides a clear and comprehensive overview of the organization's cybersecurity policies and procedures, meaning all individuals and teams know their roles and responsibilities in managing the organization's security and are working towards the same goals.
The Components of an SSP for NIST 800-171
For NIST 800-171 compliance, the SSP must include a system categorization process that identifies and classifies the organization's systems and data according to their level of security and sensitivity. This process involves assessing the risks associated with each system and data set and determining the required level of protection. The SSP must also include the security controls and measures implemented to protect each system and dataset.
Download the NIST SP 800-171 System Security Plan Template provided directly from NIST here:
The Components of an SSP for CMMC
For CMMC compliance, the SSP must include a detailed description of the organization's cybersecurity policies and procedures and the controls in place to protect against threats. The SSP must also have a system categorization process, risk management plan, and regular security assessments and testing evidence.
How To Implement And Document an SSP
There are several steps involved in implementing and documenting an SSP. These steps may vary depending on the specific requirements of the organization and the regulatory framework it must satisfy. Still, the following steps provide a general overview of the process:
- Identifying the Scope of the SSP: Determine which systems and data need to be protected and what level of security they require.
- Conducting a Risk Assessment: Analyze the potential threats and vulnerabilities to the systems and data identified in step 1.
- Develop POAMs: Based on vulnerabilities, create Plans of Action and Milestones as outlined by NIST 800-171 requirements.
- Developing Security Controls: Based on the risk assessment, create policies, procedures, and controls that protect the systems and data from those threats and vulnerabilities.
- Documenting the SSP: Write down the policies, procedures, and controls in a clear and organized manner. This will serve as your SSP document.
- Training Employees: Ensure all employees understand the SSP and their role in protecting the organization's systems and data.
- Review and Update: Review the SSP document regularly and update it as necessary to keep it current with changing technologies and threats.
It's always best to seek expert guidance to ensure the SSP document meets standards and compliance.
Unsure About Your Current SSP? We’re Here to Help.
An SSP is integral to complying with NIST 800-171 and CMMC standards. Our team of experienced security professionals can help you develop and document a comprehensive SSP that meets CMMC requirements and protects your organization's systems and data. Contact us to schedule an initial consultation today!
Additional Blog Posts

CMMC Deadlines: Defense Contractors Face High-Stakes Compliance Timelines
As the U.S. Department of Defense accelerates enforcement of the Cybersecurity Maturity Model Certification (CMMC),…
DOJ Ramps Up Cyber-Enforcement on Defense Contractors
The Department of Justice’s recent $4.6 million settlement with defense contractor MORSECORP sends a clear…
